

No Case Studies available.
No Whitepapers available.
No Videos available.
No E-books available.

25-Jul-2024
This blog explains what data catalogs are and why they are an important investment

22-Feb-2024
Open source security is a term used to describe the process of protecting your organization’s dat...

22-Dec-2023
A policy, by definition, is a statement of management intent that is mandatory for an organization.

2025-06-18
Discover how SRC’s third-party data flow management system delivers real-time visibility, control...
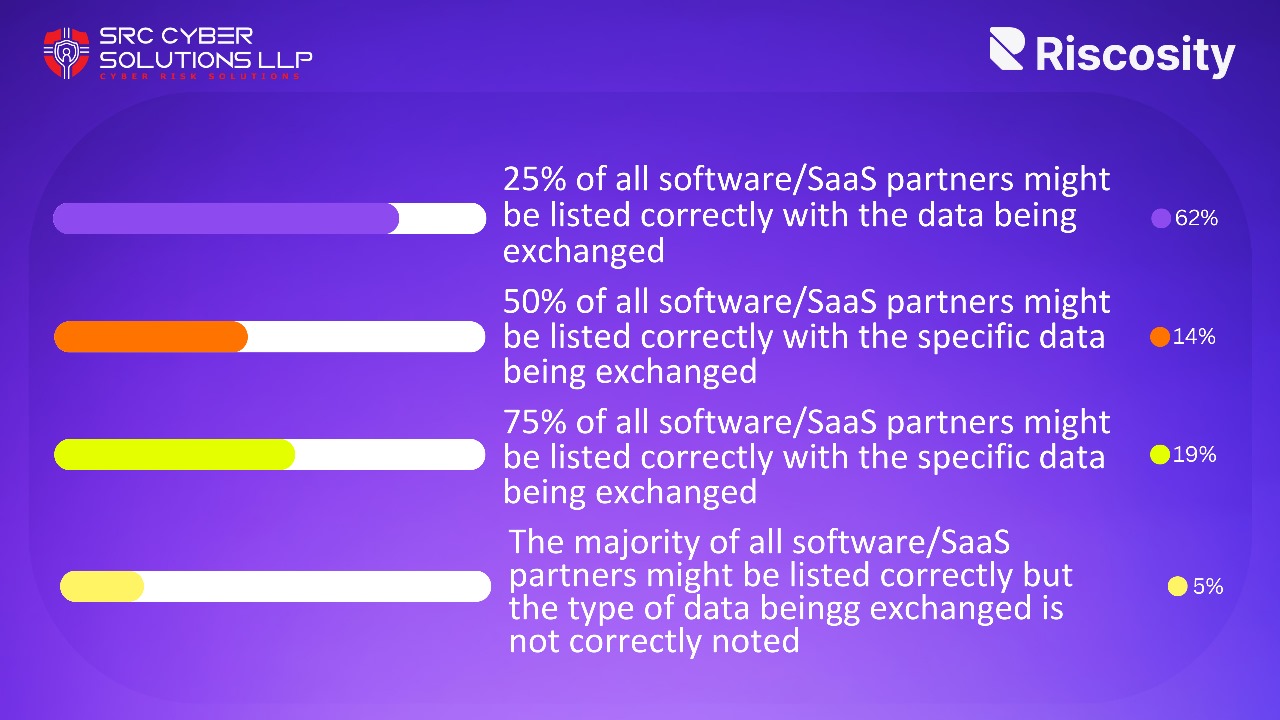
19-Jan-2024
Keeping a Pulse on All Third-Party Connections One of the main goals of information security is ...

17-Jan-2024
A comprehensive application risk assessment guide sharing tips and considerations of the process ...

12-Jan-2024
Data lineage and data provenance are related terms, but different. Lineage focuses on the origins...

11-Oct-2023
Last week, a vulnerability in the popular MOVEit managed file transfer service was exploited by t...

07-Nov-2023
Imagine a world where you confidently navigate the complexities of General Data Protection Regula...